Related Keywords
algorithm downloadsalgorithm 2 downloads
algorithm development downloads
algorithm optimization downloads
algorithm x64 downloads
md5 algorithm downloads
aes encryption algorithm downloads
optimization algorithm downloads
using aes algorithm downloads
sha 1 algorithm downloads
secure hash algorithm downloads
genetic algorithm downloads
compression algorithm downloads
genetic algorithm optimizatio downloads
reliable algorithm and all downloads
google algorithm downloads
image algorithm downloads
comparison algorithm downloads
encryption algorithm downloads
checksum algorithm downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
encryption software downloads
safe downloads
file encryption downloads
privacy downloads
decryption downloads
data encryption downloads
secure downloads
password downloads
security downloads
folder lock downloads
files downloads
recovery downloads
protection downloads
encrypt downloads
file downloads
email downloads
folder downloads
protect downloads
crack downloads
hide downloads
folders downloads
blowfish downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ Toms Hash Explorer
Toms Hash Explorer1.2 by Tom Andreas Mannerud |

|
Software Description:
... verify file integrity. Supports the most popular hashing algorithms such as MD5, SHA-1, and SHA-2 including SHA256, SHA384, and SHA512. ...
type: Freeware
Download Toms Hash Explorercategories: CRYPTO, HASH, HASHING, MD5, SHA, SHA-1, SHA-2, SHA256, SHA384, SHA512, SHANNON, ENTROPY, FILE INTEGRITY, FAST, MULTI-THREADED, FREE Add to Download Basket Report virus or spyware |
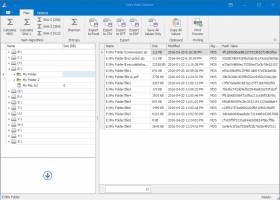 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Toms Hash Explorer full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Toms Hash Explorer license key is illegal and prevent future development of Toms Hash Explorer. Download links are directly from our mirrors or publisher's website, Toms Hash Explorer torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | August 20, 2016 |
| Filesize: | 17.44 MB |
| Language: | English |
| Platform: | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Requirements: | Microsoft .NET Framework 4.5.2 |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Toms Hash Explorer- Releases History |
| Software: | Toms Hash Explorer 1.2 |
| Date Released: | Aug 20, 2016 |
| Status: | Minor Update |
| Release Notes: | File Integrity Verification/Batch Verification |
| Software: | Toms Hash Explorer 1.1 |
| Date Released: | Apr 29, 2016 |
| Status: | New Release |
| Release Notes: | Themes/Skin Support, Drag and Drop, and File Entropy Computation using Shannon's Entropy Algorithm. |
Most popular algorithm in Encryption Tools downloads for Vista |
|
XorIt 1.9 download by Sinner Computing
... from now. This is because there is no algorithm at all, just a big key, and thus there is no pattern to follow once you have decrypted any part of ...
View Details
Download
|
 |
|
PenProtect 1.45 download by EasyLine
... using your Password and a special technique (AES algorithm 256 bit key). PenProtect requires no installation: it is a single file located in the home folder of your Flash Drive. ...
type: Demo ($19.00)
View Details
Download
categories: flash drive, USB, password, flash memory, pen drive, crypt, encrypt, decrypt, software, key, file, folder, AES, AES 256, security, cryptography, secure, stick, device, lock, guard flash drive, guard pen drive, penprotect |
 |
|
SecureCD Creator 2.0 download by KernSafe Technologies, Inc.
... SecureCD Creator use AES 256 and SHA256 bit algorithm, running at high security level. SecureCD Creator will give quadruple security for valuable data protection. Generally, SecureCD Creator can use for ...
type: Shareware ($34.90)
View Details
Download
categories: CD encryption, DVD Encryption, CD encrypt, DVD encrypt, CD password, DVD password, iso, iso9660, iso file, iso editor, iso edit, virtual CD-ROM, emulator, encrypt, encryption |
|
BestCrypt Volume Encryption 5.12.3 download by Jetico Inc
... Encryption allows encrypting data with many strong encryption algorithms. Every algorithm is implemented with the largest possible key size defined in the algorithm's specification: * AES (Rijndael) - 256-bit key. * ...
type: Trialware ($99.95)
View Details
Download
categories: Volume Encryption, encryption algorithm, encryption key, Encryption, Encrypt, Encrypter |
 |
|
Lavasoft File Shredder 2009 7.7.0.2 download by Lavasoft AB
... and supports the Department of Defence (DoD) shredding algorithm, using seven rounds of overwriting, as well as all other advanced standards. Features: Take control of your confidential information ...
type: Trialware ($29.95)
View Details
Download
categories: flie shredder, delete file, shred file, shredder, shred, delete |
 |
|
Encrypting Safe 1.1 download by Google
... from others using the Encrypting Decrypting symmetric key algorithm, it's easy to transfer your note form source ... Smart Phone Behind: Using Symmetric key Algorithm for Encrypting and Decrypting note Features: - ...
type: Freeware
View Details
Download
categories: encrypt text, text encryption, Encrypting Decrypting symmetric key algorithm, encrypt, encryption, encryptor |
 |
|
SteadyCrypt 2.4 download by Marvin Hoffmann & Jörg Harr
... usage. As far as features, tools and encryption algorithm are concerned, it is not comparable to widely used TrueCrypt, but users who wont like to follow lengthy procedure in TrueCrypt ...
type: Freeware
View Details
Download
categories: file encryption, data crypter, encrypt information, encrypt, encryption, encryptor |
 |
|
InfoLock 6.2 download by Ben Hershey
... files, as this is necessary for the superior-security algorithm. Key Features: --Ultra lightweight: no installation, no ... --Simple and straitforward to use. --Very secure unique algorithm. --Encrypted code consists of 1 line of text ...
View Details
Download
|
 |
|
Paranoia Text Encryption for PC 15.0.4 download by Paranoia Works
... unwanted readers. Texts are encrypted using strong encryption algorithms: AES (Rijndael) 256bits, RC6 256bit, Serpent 256bit, Blowfish ... text within an image - JPG). A steganographic algorithm (F5 algorithm) is used in combination with chosen ...
type: Freeware
View Details
Download
categories: encryption, encrypter, encryptor, encrypt, note, notes, text, texts, messages, chat, email, emails, sms, social, ciphering, encipher, aes, blowfish, threefish, serpent, 256, 512, 1024, bit, bits, steganography, JPG, cryptocurrency, seed, mnemonic, key, keys, safe, vault, password |
 |
|
EaseFilter Auto File Encryption 5.6.1.1 download by EaseFilter Inc.
... encrypt or decrypt the data with AES encryption algorithm. Atuo file encryption protects data 'at rest', meaning ... to access the encrypted files. Supported strong cryptographic algorithm Rijndael is a high security algorithm which was ...
type: Freeware
View Details
Download
categories: System Filter Driver SDK, File system control filter driver SDK, Continuous protection, TRANSPARENT ENCRYPTION, user access controls, Source Code |
 |