Related Keywords
algorithms downloadscryptographic algorithms downloads
genetic algorithms downloads
comparison algorithms downloads
hash algorithms downloads
trading algorithms downloads
forecasting algorithms downloads
multiple algorithms downloads
geo algorithms downloads
evolutionary algorithms downloads
Top Software Keywords
decrypt downloadsencryption downloads
aes downloads
encryption software downloads
safe downloads
file encryption downloads
privacy downloads
decryption downloads
data encryption downloads
secure downloads
password downloads
security downloads
folder lock downloads
files downloads
recovery downloads
protection downloads
encrypt downloads
file downloads
email downloads
folder downloads
protect downloads
crack downloads
hide downloads
folders downloads
blowfish downloads
lock downloads
lock folder downloads
recover downloads
rijndael downloads
des downloads
Vista Download
Vista downloadVista antivirus download
Vista wallpaper download
Vista wallpapers download
Vista themes download
Vista pack download
Vista ultimate download
Vista home download
Vista basic download
Vista business download
Vista x64 download
Vista transformation download
Vista transformation pack download
Vista boot download
Vista dvd download
Vista sidebar download
Vista aero download
Vista product key download
Top Downloads
Top Rated
Navigation: Home
\ Security & Privacy
\ Encryption Tools \ Toms Hash Explorer
Toms Hash Explorer1.2 by Tom Andreas Mannerud |

|
Software Description:
... verify file integrity. Supports the most popular hashing algorithms such as MD5, SHA-1, and SHA-2 including SHA256, SHA384, and SHA512. ...
type: Freeware
Download Toms Hash Explorercategories: CRYPTO, HASH, HASHING, MD5, SHA, SHA-1, SHA-2, SHA256, SHA384, SHA512, SHANNON, ENTROPY, FILE INTEGRITY, FAST, MULTI-THREADED, FREE Add to Download Basket Report virus or spyware |
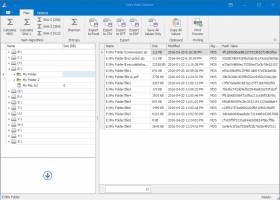 [ Zoom screenshot ] |
|
| Software Info | |
|
Best Vista Download periodically updates pricing and software information of Toms Hash Explorer full version from the publisher,
but some information may be out-of-date. You should confirm all information. Software piracy is theft, using crack, warez passwords, patches, serial numbers, registration codes, key generator, keymaker or keygen for Toms Hash Explorer license key is illegal and prevent future development of Toms Hash Explorer. Download links are directly from our mirrors or publisher's website, Toms Hash Explorer torrent files or shared files from rapidshare, yousendit or megaupload are not allowed! |
|
| Released: | August 20, 2016 |
| Filesize: | 17.44 MB |
| Language: | English |
| Platform: | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Requirements: | Microsoft .NET Framework 4.5.2 |
| Install | Install and Uninstall |
| Add Your Review or Windows Vista Compatibility Report |
Toms Hash Explorer- Releases History |
| Software: | Toms Hash Explorer 1.2 |
| Date Released: | Aug 20, 2016 |
| Status: | Minor Update |
| Release Notes: | File Integrity Verification/Batch Verification |
| Software: | Toms Hash Explorer 1.1 |
| Date Released: | Apr 29, 2016 |
| Status: | New Release |
| Release Notes: | Themes/Skin Support, Drag and Drop, and File Entropy Computation using Shannon's Entropy Algorithm. |
Most popular algorithms in Encryption Tools downloads for Vista |
|
Aloaha Crypt Disk 6.0.16 download by Aloaha Limited / CodeB
... volume (steganography) with second smart card - Encryption algorithms: AES-256, Serpent, and Twofish. Mode of operation: XTS. Requirements - Windows XP, Vista, 2008, 7, 8, 2008(r2), 2012 - Encryption Certificate ...
type: Freeware
View Details
Download
categories: disk, encryption, volume, usb, stick, smart, card, smart card, smartcard, certificate |
 |
|
BestCrypt Volume Encryption 5.12.3 download by Jetico Inc
... Encryption allows encrypting data with many strong encryption algorithms. Every algorithm is implemented with the largest possible ... Encryption utilizes XTS Encryption Mode with all encryption algorithms listed above. XTS Mode is designed specifically for ...
type: Trialware ($99.95)
View Details
Download
categories: Volume Encryption, encryption algorithm, encryption key, Encryption, Encrypt, Encrypter |
 |
|
Kruptos 2 7.0.0.1 download by Kruptos 2
... backdoors Uses proven and unbroken 256bit file encryption algorithms, no hidden back doors, secret keys or NSA agreements ...
type: Trialware ($10.99)
View Details
Download
categories: encryption solution, process file, securely process, encryption, process, decryption |
 |
|
Aloaha Smartcard Connector 6.0.60 download by Wrocklage Intermedia GmbH
... PC/SC II Microsoft CSP PKCS 11 PKI Supported Algorithms: RSA 1024 - 2048 DES & Triple-DES RC2 & RC4 SHA-1 & SHA-256 Approx. 45 Smartcards supported: SuisseID, German e-ID (nPA), ...
type: Shareware ($57.40)
View Details
Download
categories: smart card, csp, pkcs11, HBA, eGK, sagemorga, qs1, belpic, infocamere, telesec, d-trust, multicard, p7m, p7s, pkcs7 |
 |
|
Batch File Encrypt Free 5.0.127 download by BinaryMark
... using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for ...
type: Shareware
View Details
Download
categories: batch, multiple, bulk, mass, files, encrypt, file encryption, decrypt, aes, 3-des, des, rc2, symmetric, algorithm, cryptographic, key, password, vector, bit strength |
 |
|
Advanced Encryption Package 2008 Professional 4.8.7 download by InterCrypto Ltd
... your private files. Program includes 17(!) undustrial encryption algorithms: DESX, BLOWFISH, RIJNDAEL(AES), CAST, 3-DES, RC2, DIAMOND2, TEA, ... These keys are large mathematically-related numbers derived from algorithms that form a unique pair. Either key may ...
type: Shareware ($49.95)
View Details
Download
categories: encrypt, encryptor, password, protect, blowfish, extracted, ecnrypted, shred, blowfish.zip, unzip, pkzip, winzip, blowfish, twofish, rijndael, cast, mars, serpent, tea, desx, gost, rc2 |
 |
|
TrueCrypt 7.2 download by TrueCrypt Foundation
... (steganography) and hidden operating system. * Encryption algorithms: AES-256, Serpent, and Twofish. Mode of operation: XTS. ...
type: Freeware
View Details
Download
categories: disk encryptor, virtual disk creator, data encryptor, encryptor, decryptor, encrypt |
 |
|
Hard Drive Eraser 2.0 download by Hard Drive Eraser
... not be recovered. Hard Drive Eraser uses powerful algorithms with multiple passes to assure permanent data removal. Hard Drive Eraser does not contain adware, it is released under General Public ...
View Details
Download
|
 |
|
BestCrypt Container Encryption 9.08.9 download by Jetico Inc. Oy
... and Linux by utilizing a wide variety of algorithms (AES, Blowfish, Twofish, CAST, GOST 28147-89, Triple-Des, Serpent) and the largest possible key sizes with XTS, LRW and CBC encryption modes. ...
type: Shareware ($59.95)
View Details
Download
categories: data encryption, file encryption, encrypt files, best encryption software, folder encryption, prevent data breaches, truecrypt alternative |
 |
|
VSEncryptor 64-bit 2.7.3.527 download by Lokibit.com
... box. VSEncryptor supports a variety of encryption algorithms, including AES-128, AES-192, AES-256, RC2, RC4, DES and Triple DES. ...
View Details
Download
|
 |